Hybrid Authentication
Starting with B2C Commerce version 25.3, hybrid authentication (Hybrid Auth) replaces the Plugin SLAS cartridge option. To take advantage of the improved performance and streamlined workflow, we recommend migrating to Hybrid Auth.
Only existing customers can access some of the links on this page. Visit Salesforce Commerce Cloud GitHub Repositories and Access for information about how to get access to the Commerce Cloud repositories.
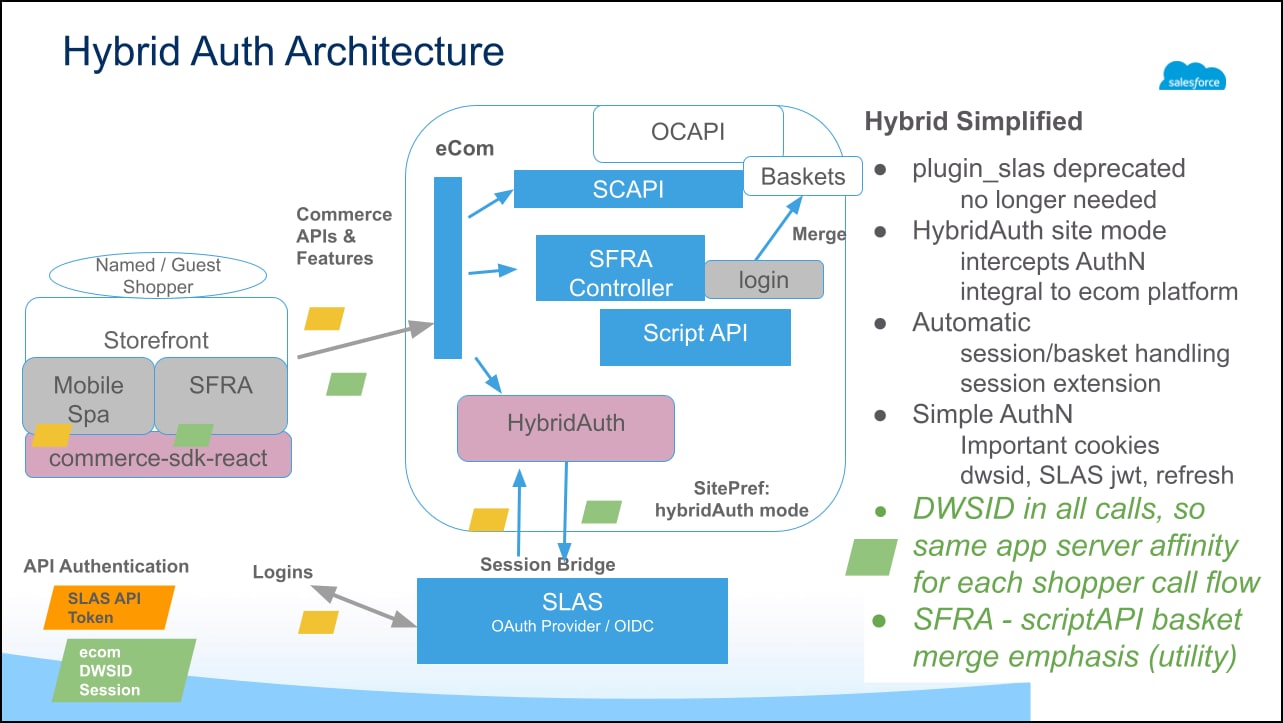
Hybrid Auth is a standalone solution for implementations that need both Storefront Reference Architecture (SFRA)/SiteGenesis authorization and Shopper Login and API Access Service (SLAS) authorization. This means you need both a dwsid (SFRA/SiteGenesis) and a JSON Web Token (SLAS), and these tokens must be kept in sync.
Hybrid Auth fully replaces Plugin SLAS and improves performance and stability of hybrid storefronts by moving the feature directly into the B2C Commerce platform.
Hybrid Auth is designed for various use cases, all of which involve using both SFRA/SiteGenesis and SLAS.
- Hybrid implementation (partial headless site, which could include PWA Kit or other headless solution): Some parts of your site (like product list pages and product detail pages) are done in a headless application, while the other parts of the site (like cart and checkout) remain in SFRA or SiteGenesis.
- If you plan to use any headless technology for part of your site (a hybrid setup with SFRA/SiteGenesis), you need Hybrid Auth.
- SFRA/SiteGenesis: You can use Hybrid Auth with an SFRA/SiteGenesis site alone, to take advantage of SLAS features, including longer session durations (up to 90 days) and federated login.
For upgrading a PWA Kit v2.x project to Hybrid Auth, see Hybrid Auth Implementation with PWA Kit v2.x.
For non-PWA kit customers, if you're using HybridAuth and the dwsid cookie exists, include the sfdc_dwsid header with the cookie dwsid value for all SCAPI calls.
This image provides an example hybrid B2C Commerce stack using Hybrid Auth and Composable Storefront. Composable Storefront serves the top of the funnel as a headless implementation and uses SCAPI to communicate with the B2C Commerce instance. An SFRA storefront running cart and checkout communicates directly with the B2C Commerce instance. The SFRA project uses Hybrid Auth to facilitate session bridging between the two infrastructures. A CDN (eCDN or your own stacked CDN) routes traffic to the two infrastructures depending on the shopper's requested path.
Launch faster with out-of-the-box authentication, ensuring automatic data synchronization between SFRA and Composable Storefront pages. You no longer need Plugin SLAS!
Shoppers can navigate across your hybrid site with no disruption or loss of data. Synchronization is expanded to include Shopper Context session attributes and support for consistent analytics.
Whether you are using SiteGenesis or SFRA, we have you covered with a fully supported and productized solution to ease your path to Composable Storefront success.
-
If you plan to use Hybrid Auth with PWA Kit, make sure your site is built with:
commerce-sdk-react@3.3.0or later- Progressive Web App (PWA) Kit version 3.10 or later
For details, see Get Started with Composable Storefront.
-
Set up a SLAS Client:
- Hybrid Auth supports both SLAS public and private clients. Create a SLAS client if you don't already have one. For details, see: Authorization for Shopper APIs.
-
Enable session bridging:
- Update the scope of the SLAS client being used for Hybrid Auth to include
sfcc.session_bridge. For details, see Shopper Login and API Service (SLAS) Overview. - Make sure that the Client ID used in Hybrid Auth is the same as the one used in your PWA Kit/headless application.
- Update the scope of the SLAS client being used for Hybrid Auth to include
-
(Optional) Starting with B2C Commerce version 25.8, Hybrid Auth supports Third-Party IDP and Social Login. You can set up Third-Party Login/Social Login using SLAS:
- If you're using Third-Party or Social Login, you must perform all Third Party IDP interactions with SLAS. To set up a supported IDP:
- Create an OAuth client in the IDP's administration portal.
- Use the SLAS Admin API or SLAS Admin UI to configure the IDP for a SLAS tenant. In the SLAS Admin UI, navigate to the Idps tab and then select Add Idp.
-
The IDP name in the SLAS Admin configuration is case sensitive and must match the OAuth Provider ID in SFRA/SiteGenesis.
-
- Add the SFRA/SiteGenesis Login-OAuthReentry redirect URI to the SLAS Client ID created in the first step in the SLAS Admin UI, for example:
https://<Site Host Name>/on/demandware.store/Sites-<Site Id>-Site/<locale>/Login-OAuthReentry
- Add the SFRA/SiteGenesis Login-OAuthReentry redirect URI in the IDP's administration portal, for example:
https://<Site Host Name>/on/demandware.store/Sites-<Site Id>-Site/<locale>/Login-OAuthReentry<IDPProviderId>
- If you're using Third-Party or Social Login, you must perform all Third Party IDP interactions with SLAS. To set up a supported IDP:
-
Configure Business Manager:
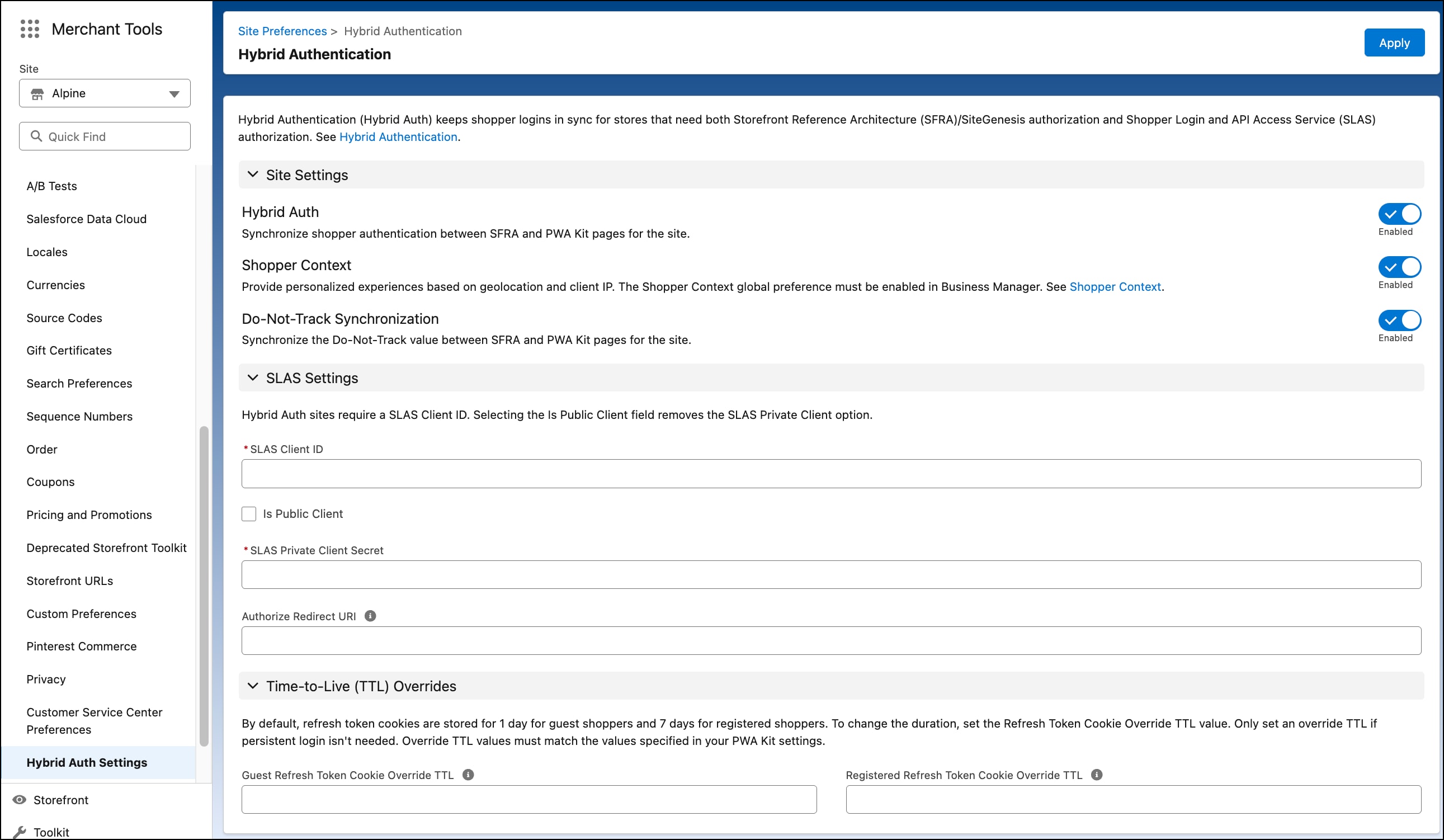
- In Business Manager, go to Merchant Tools.
- Select a site that matches your setup, for example:
RefArch/RefArchGlobal/SiteGenesisGlobal. - In the quick-find box, search for “hybrid auth”. Select Hybrid Auth Settings in the filtered results. For B2C Commerce version 25.10, the Business Manager interface has been updated. If you are using a version earlier than 25.10, the options in the interface are slightly different.
- Enable the Hybrid Auth toggle.
- Enter your SLAS client ID, which can be for either a private client or a public client.
- If your SLAS client ID is a public client, select the Is Public Client checkbox.
- If your SLAS client ID is a private client, enter your SLAS private client secret.
- Enable the Shopper Context toggle to take advantage of the Shopper Context features with Hybrid Auth.
- Enable the Do-Not-Track Synchronization toggle to take advantage of DNT sync with Hybrid Auth.
- Starting with B2C Commerce version 25.8.1, to change the guest refresh token TTL from the default 30 days to a lesser value, enter a value between 360 and 43200 (6 hours and 30 days in minutes) in the Guest Refresh Token Cookie Override TTL field.
- For this to be effective, the PWA Kit cookie TTL for guest refresh token must be configured to the same value.
- Making this change effectively reduces the persistent session time for the guest shopper.
- Starting with B2C Commerce version 25.8.1, to change the registered refresh token TTL from the default 90 days to a lesser value, enter a value between 360 and 129600 (6 hours and 90 days in minutes) in the Registered Refresh Token Cookie Override TTL field.
- For this to be effective, the PWA Kit cookie TTL for the registered refresh token must be configured to the same value.
- Making this change effectively reduces the persistent session time for the registered shopper.
- Click Apply.
- Select a site that matches your setup, for example:
- In Business Manager, click App Launcher
 and then select Administration.
and then select Administration.
- In the quick-find box, search for Security.
- Select the Access Restriction tab.
- Enable the Enforce HTTPS checkbox.
- Click Apply.
- In Business Manager, go to Merchant Tools.
-
Remove Plugin SLAS from the cartridge path. With the migration to B2C Commerce Hybrid Auth, Plugin SLAS is no longer required.
Perform the following steps if you have ever used Plugin SLAS. If you're new to hybrid storefront implementations, and are now getting started with Hybrid Auth, you can skip these step. This step applies only if you previously used Plugin SLAS in your hybrid storefront. If you have a new hybrid storefront and you never used Plugin SLAS before, you can skip this step.
- Click App Launcher
 and then select Administration > Sites > Manage Sites > Select Site.
and then select Administration > Sites > Manage Sites > Select Site. - Go to the Settings Tab.
- Remove
plugin_slasfrom the cartridge path. - For code customizations:
- If you have shopper authentication code customizations that aren't specific to Plugin SLAS, they should continue to work as is.
- If you have customizations that are specific to Plugin SLAS, review those changes, because they might not be required or you might need to re-implement the changes in a different cartridge.
- Following best practices, implement code customizations in a separate cartridge instead of directly modifying out-of-the-box SFRA cartridge code.
- Make sure that none of your custom cartridge code calls session bridging endpoints, because this can cause problems in shopper sessions. Hybrid Auth handles session bridging for you.
- Click App Launcher
-
For Composable Storefront: Handle cookie responses in the client browser:
- As part of Hybrid Auth, SLAS token calls now include the
dwsidin theSet-Cookieresponse header. Ensure theSet-Cookieheaders are respected from SLAS API calls and the cookies are set in the browser. - NOTE: If you are using Commerce Cloud React SDK with the Composable Storefront, this cookie handling is done for you with PWA Kit v3.9 and later.
- As part of Hybrid Auth, SLAS token calls now include the
-
For Composable Storefront: Set up Embedded Content Delivery Network (eCDN) Origin Rules:
-
Configure the embedded content delivery network (eCDN) to send page requests at the top of the funnel to the Composable Storefront: home page (
/), the category listing page (/category), and the product details page (/product). These pages are deployed to a Managed Runtime (MRT) environment running on mystorefront.mobify-storefront.com. When the shopper decides to make a purchase, the eCDN redirects the shopper to the existing SFRA/SG checkout page running onwww.mystorefront.com. -
To use Commerce API CDN Zones to route traffic to Managed Runtime, follow the steps in CDN APIs for Hybrid Implementations.
- Make sure you provide these values for new rules:
- Rule Name: Any name that helps you identify this ruleset is for hybrid storefronts. You can have more than one ruleset for a storefront.
- Enable Rule Once Saved: Select this checkbox to immediately apply the ruleset when you click Save.
- Hostnames: Click Select Hostnames and select the hostname for your hybrid storefront.
- MRT Origin: Your MRT storefront domain, which you can find in Environment Settings in Runtime Admin.
- Rule Expression: Your origin ruleset.
- Make sure you provide these values for new rules:
-
For more information about routing traffic to MRT, see:
-
-
For Composable Storefront: Create a PWA Kit Retail React App:
-
Do either of these steps:
-
Create a Retail React App with SLAS public or private client configuration
- Create a PWA Kit app by running the following generator command in a terminal window:
npx @salesforce/pwa-kit-create-app my-hybrid-storefront - Select The Retail app using your own Commerce Cloud instance.
- Follow the instructions in the terminal.
- Create a PWA Kit app by running the following generator command in a terminal window:
-
Alternatively, generate a Retail React App with a preset configuration and change the SLAS client ID to your public or private client once the app is generated.
- Follow the steps in the Quick Start.
- Use a SLAS public or private client.
- Make sure the SLAS Client used for Hybrid Auth includes the
sfcc.session_bridgescope.
-
-
-
For Composable Storefront: Update PWA Kit Routes:
-
By default, PWA Kit uses the History API for navigation. When a shopper clicks a link made with a React Router component, it triggers a soft navigation to the component matching the path in the route object defined in
app/routes.jsx. To link to a non-PWA Kit page (one powered by SFRA, for example), remove any route matching the URL pathname fromapp/routes.jsx.-
If your PWA Kit project was generated with version 3.x of the Retail React App template using template extensibility, you can override the
overrides/app/routes.jsxfile to filter out links to non-PWA Kit pages using JavaScript.- We've created an example override of the
overrides/app/routes.jsxfile with all the changes in place to filter out/cartand/checkoutroutes. Customize the example override code in this public gist to filter out links to non-PWA Kit pages.
- We've created an example override of the
-
Update the PWA catch-all route (
/*) inapp/routes.jsx. In this example, replace the PWA<PageNotFound />component with a redirect to the default origin.
-
-
-
For Composable Storefront: Upgrade
@salesforce/commerce-sdk-react:- If your site uses commerce-sdk-react, upgrade to
@salesforce/commerce-sdk-react@3.3.0or later.
- If your site uses commerce-sdk-react, upgrade to
-
For Composable Storefront: Enable cookies on Managed Runtime:
-
When Hybrid Auth is enabled, SLAS
/oauth2/tokenrequests contain a session-bridgeddwsidusing theSet-Cookieheader in the response. -
In Managed Runtime, enable cookie passthrough:
- Log in to Managed Runtime Admin.
- Navigate to your project and environment.
- Select Environment Settings.
- Scroll to the Advanced section and select the Edit button.
- Enable the switch next to Cookies.
- Scroll back to the Advanced section and select Update.
- Wait for your storefront bundle to redeploy.
-
-
For Composable Storefront: Use Commerce API CDN Zones to route traffic to Managed Runtime. See CDN APIs for Phased Headless Rollouts.
-
(Optional) For Composable Storefront: Get analytics using Einstein Activities for Phased Headless Rollouts.
-
Verify your Hybrid Auth setup:
- Go to your storefront using the vanity domain configured in eCDN in a browser.
- Navigate to a page on SFRA/Sitegenesis.
- Open Developer Tools in the browser to inspect cookies. Confirm the following cookies have been set:
cc-nx-g_{Site_ID}- Guest Refresh Tokendwsid- B2C Commerce session IDusid- SLAS Customer IDcc-at_{Site_ID}- SLAS Access Token (This cookie only shows up when the user lands on an SFRA page. This cookie is not seen when navigating from a PWA Kit page to an SFRA page.)
- Navigate to any PWA Kit page. Verify these cookies:
cc-nx-g_{SiteID}: Should be the same.dwsid: Should be the same.usid_{SiteID}: Should be the same.cc-at_{SiteID}: You no longer see this cookie as the cookie was consumed by PWA Kit and the access token was moved to localStorage. You can inspect localstorage to confirm the accesstoken{SiteID} value matches what you originally had in the cc-at_{SiteID} cookie.
- Now switch over to the Network Tab in your browser’s Developer Tools.
- Add an item to the cart on PWA Kit.
- Inspect the SCAPI request in the network tab for Add to Cart. This is a critical header required to maintain hybrid stability in production at scale when your traffic might be distributed to multiple appservers.
- In the headers section, locate the Request Headers.
- If you are using PWA Kit, confirm you see the
sfdc_dwsidheader set to thedwsidcookie value as seen previously. If you are NOT using PWA Kit, set this from your headless application if thedwsidcookie is available.
We recommend testing your hybrid setup in SIG environments, such ODS or a local development server. To do this, you must set up a reverse proxy, such as the hybrid proxy feature in PWA Kit, because eCDN doesn't support SIG environments. To set up and test your hybrid app locally on a SIG instance, use hybrid proxy or CDN to split traffic. Hybrid proxy is available starting in PWA Kit v3.14 in the pwa-kit-runtime package. Hybrid proxy enables you to develop and test hybrid shopper flows across PWA Kit and SFRA/SiteGenesis.
Enable hybrid proxy for SIG instances only. On PIG instances, use eCDN to direct requests to the PWA Kit Composable storefront or SFRA/SiteGenesis store. Don't enable hybrid proxy on PIG instances. Because hybrid proxy sets the localAllowCookies: true variable, it can cause security issues on PIG instances.
Use hybrid auth with hybrid proxy. Hybrid auth is a replacement for the Plugin SLAS cartridge option. If you use Plugin SLAS, replace it with hybrid proxy. See Hybrid Auth Overview.
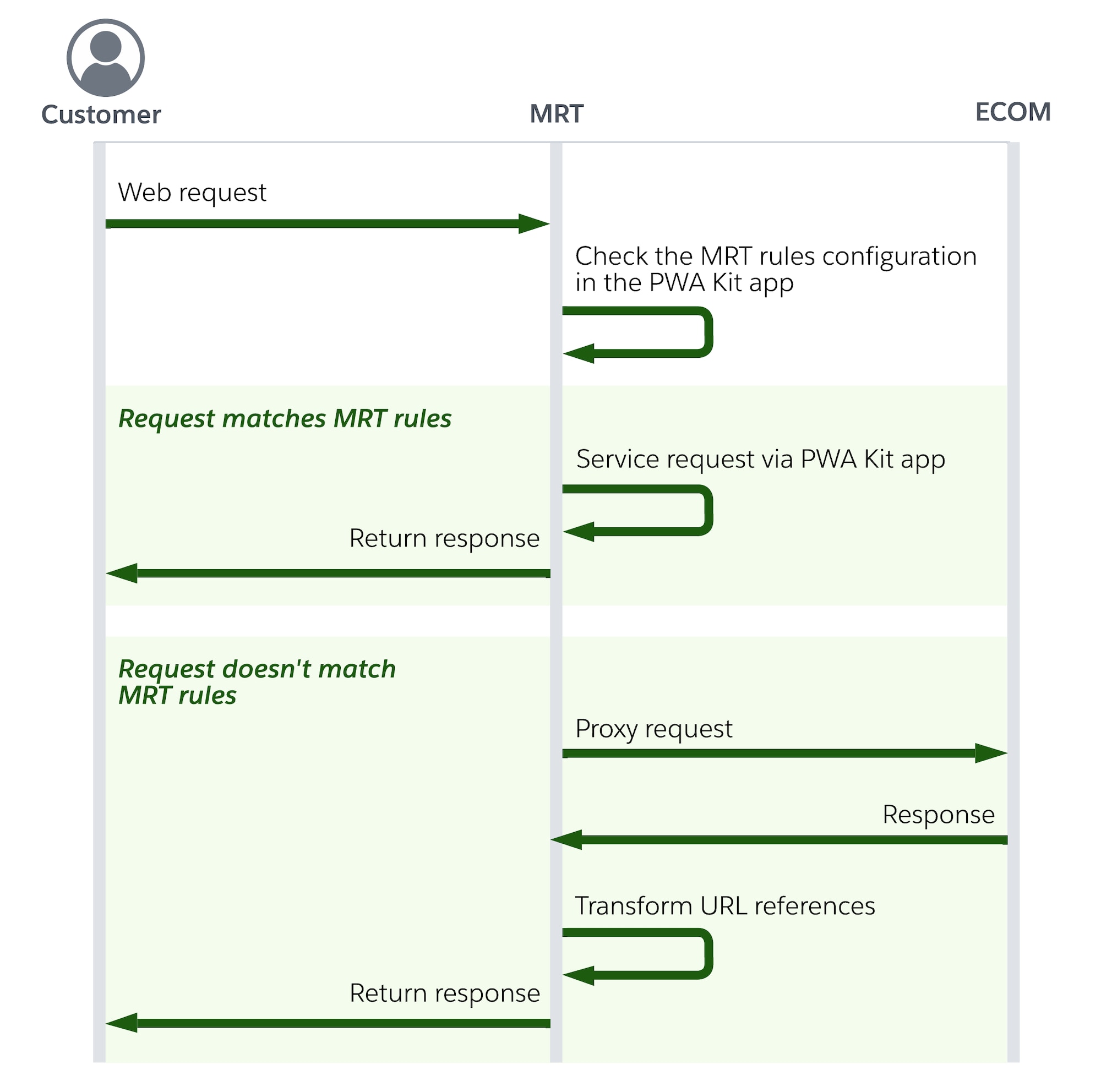
This diagram shows the sequence of requests and responses when a proxy routes an incoming page request for a hybrid app for a SIG instance. If the request matches MRT rules, it is serviced via a PWA Kit app. Otherwise, if the request doesn't match MRT rules, a proxy request is sent to the B2C Commerce instance. Next, URL references are transformed and a response is returned.
Follow these steps to enable hybrid proxy locally.
-
Upgrade
pwa-kit-runtimepackage dependency to v3.14.0 or later. -
Configure the
hybridProxyvalue in your composable storefrontssr.jsfor server-side reverse proxy.localAllowCookies: truehybridProxy.enabled: truehybridProxy.sfccOrigin: [your SFCC store]
-
Update
default.jsto configure client-side routing.- Update
app.commerceAPI.parametersto point to the correct commerceAPI SIG instance. - Add
app.enableHybrid: trueso that you can turn it on/off.
- Update
-
Uncomment
hybridAuthEnabledin_app-config.js. -
If the current site has Hybrid Auth enabled, in
app/components/_app-config/index.jsx, uncommenthybridAuthEnabled. Don't set this flag for hybrid storefronts using Plugin SLAS. -
Update
routes.jsxto exclude routes on the PWA-Kit. For reference, see https://gist.github.com/clavery/c0c8689ee852876cfc5b297985c4300e#file-routes-jsx-L116.
This example removes the /cart and /checkout routes from PWA Kit store and uses capture all route \* to trigger server-side rendering of proxied SFCC cart and checkout page.
If you deploy the changes to the Managed Runtime environment, make these additional changes.
- Follow step 11 in Step 1: Set Up Your Storefront with Hybrid Auth to enable cookies, or use this API call to enable cookies in your Managed Runtime Environment:
- Configure a Managed Runtime proxy with path
dwrestaticthat points to your SFCC instance.
You can configure your ODS to use an alias's configuration that is similar to your production configuration. This can help to keep your local and production setups identical. For instance by configuring your sandbox such that your hybrid site is available at the / URI ensures that URLs sent by pwa-kit don't need to be translated to include the site ID. This is usually how a production site is configured.
To enable aliases in Business Manager, follow instructions in this module for Salesforce B2C Commerce Hostname Aliases on Trailhead.
You can configure your PWA Kit routes configuration to prefix all outgoing URLs (for example, those intended for SFRA) to include the /s/SiteID prefix. This ensures that your instance receives controller URLs in a manner normally used on sandboxes without needing to explicitly configure hostname aliases. Note that this may not be appropriate for production configuration so you may want to have a different catch-all route for production vs sandbox deployments.
To configure route prefixes, update the PWA catch-all route (/*) in app/routes.jsx or overrides/app/routes.jsx.
The B2C Commerce platform provides a default, out-of-the-box implementation for merging baskets. Some customers need further customization and can use the sample implementation in Github GIST, which behaves like the default implementation, making it an ideal starting point for customization.
After a guest shopper logs in as a registered shopper, manage the shopper basket with the dw.order.mergeBasket hook (added in B2C Commerce version 25.10). You can invoke this merge hook using either of these options:
- With a REST API call for headless storefronts
- Within the controller logic for non-headless storefronts
After invoking the hook, verify that the guest shopper's basket is appropriately combined with the registered shopper's basket.
When you use the transferBasket endpoint with the parameter merge=true, the guest basket is transferred and becomes the current basket. The dw.order.mergeBasket hook is then invoked, which merges the registered shopper's basket into the current basket. This API behavior is described in the transferBasket specification.
To add the basket merge hook into an existing controller, use the Script API to transfer the basket from the guest shopper to the registered shopper by calling BasketMgr.getCurrentBasket(). Personal information, such as payment/address information, is removed from the guest basket, and it becomes the current basket. Invoke the dw.order.mergeBasket hook to process the merge ensuring a seamless and consistent shopper experience. Use BasketMgr.getStoredBasket() to access the registered shopper's basket, which is deleted when the request ends.
For example: to add the basket merge hook for Account-Login, append the merge handling to the login function.The Github GIST contains a detailed explanation how to accomplish this, but the following example provides a quick summary for how baskets can be obtained and merged using Script API with the dw.order.mergeBasket hook:
For basket best practices in a hybrid implementation, see Hybrid Implementation Guidance.
For Hybrid Auth, we recommend the use of Shopper Context to drive geolocation-based personalizations for:
- Promotions and other experiences based on
request.geolocation.*attributes in Customer Groups - Region-specific content based on client IP
To ensure that both SCAPI and controller calls use the same geolocation and maintain consistency across a hybrid storefront:
-
Call Shopper Context with the
clientIp. -
Set the
evaluateContextWithClientIpquery parameter totrue.You must set&evaluateContextWithClientIp=truefor the IP-related context features to work correctly. -
For example:
For additional details, see:
- Shopper Context Guides
- Shopper Context API Docs
- Shopper Context Script API You can use the Shopper Context Script API to personalize shopper experiences for hybrid implementations that use SFRA/SiteGenesis pages.
To enable/disable DNT synchronization in Business Manager, navigate to Merchant Tools > Select Site > Site Preferences > Hybrid Auth Settings.
SFRA-only sites: the DNT value is automatically synchronized to the extended session, ensuring a seamless experience across sessions.
SFRA and PWA Kit hybrid implementations (new and existing): when you enable both Hybrid Auth and DNT synchronization, the tracking consent provided by a shopper on one site is automatically synchronized with the other site. For example, in a hybrid site where the home page runs on PWA Kit and the cart page runs on SFRA:
- On the home page (PWA Kit), the shopper is presented with a consent form and provides their tracking preference.
- When the shopper navigates to the cart page (SFRA), the DNT value from PWA Kit is synchronized with SFRA.
- As a result, the SFRA cart page does not prompt the shopper for tracking consent again.
SFRA and a non-PWA Kit headless hybrid implementations (new and existing): you can leverage the DNT synchronization implemented in the platform provided that:
- SFRA uses the default DNT implementation. For details, see Consent Tracking in SFRA.
- Your non-PWA Kit headless solution implements DNT similar to PWA Kit. For details, see Default Tracking Consent Implementation.
Important: If you customize the default DNT implementation, the default synchronization might not be required nor work as expected. In such cases, you can disable DNT synchronization using a site preference. You can still enable Hybrid Auth even if DNT synchronization is turned off.
If you have customized or plan to customize the default DNT implementation, the default synchronization might not be required nor work as expected. In such cases, you can disable DNT synchronization using a site preference. You can still enable hybrid auth even if DNT synchronization is turned off.
There is a key difference in DNT cookie expiration between SFRA and PWA Kit:
- SFRA sets the DNT cookie to expire at the end of the session.
- PWA Kit sets the expiration to match the refresh token's lifespan (for example, 30 days for guest users).
When a shopper moves from a PWA Kit page to an SFRA page, the DNT cookie's expiration changes from the refresh token's expiry to a session-based expiry. If the shopper closes the browser, the cookie is deleted. As a result, when the shopper returns, the tracking consent popup/banner is displayed again as expected.
The following table compares PWA Kit feature support for Plugin SLAS versus Hybrid Auth.
| Feature Name | Supported in PWA Kit w. Plugin SLAS | Supported in PWA Kit w. Hybrid Auth | Notes |
|---|---|---|---|
| SiteGenesis | N | Y | |
| Third Party IDPs and Social Login | N | Y |
|
| Passwordless Login | N | N | |
| SLAS Private Clients | Y | Y | |
| SLAS Public Clients | Y | Y | |
| SLAS Trusted System (TSOB) | N | Y | |
| Script API "Remember Me" functionality | N | N/A
| |
| PWA Kit Version 2.x | Y | Y | |
| PWA Kit Version 3.x | Y | Y | salesforce/commerce-sdk-react v3.3.0 comes packaged with PWA Kit 3.10.0. |
| Do Not Track (DNT) | N | Y | You must perform specific steps to enable and synchronize DNT. See the documentation guide. |
| Shopper Context | N | Y |
|
| Controller exclusion | Y | N | In Hybrid Auth, there is no need to exclude any controllers. |
| Cookie setting customization | Y, via customization | N/A | In Hybrid Auth, unlike plugin_SLAS, you no longer have access to the cookie object and can no longer override cookie settings. |
| Agent/Order On Behalf Of (OOBO) | N | N | Agent/OOBO is not yet supported out of the box. In Hybrid Auth, Agent/OOBO support using the Customer Service Center in Business Manager is planned for a future release. If your site uses a third-party cartridge for Agent/OOBO, make sure that you perform testing in a local environment before deploying to your live site. |
*Support is planned for a future release.